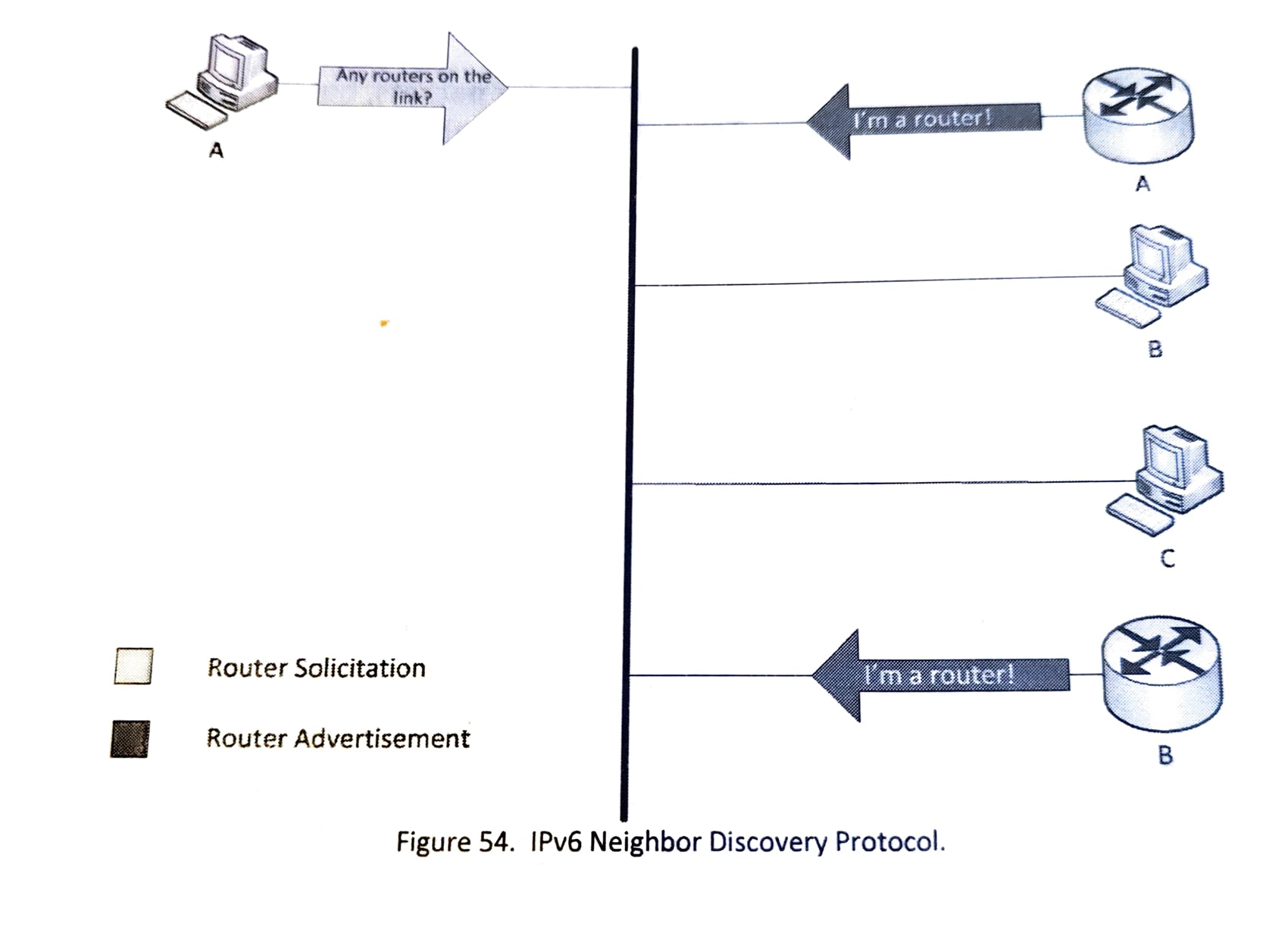
Neighbor Discovery Protocol¶
Address Spoofing: In IPv6, hosts can automatically configure their IPv6 addresses using the Stateless Address Autoconfiguration (SLAAC) mechanism, which relies on NDP. However, this also opens a door for attackers to exploit weaknesses in NDP. They can spoof IPv6 addresses, either by claiming ownership of legitimate addresses or by generating arbitrary IPv6 addresses. This can lead to serious security breaches, such as bypassing network access controls, evading detection, and launching various types of attacks, including reconnaissance, unauthorized access, and traffic interception.
Router Advertisement (RA) Spoofing: IPv6 routers use Router Advertisement (RA) messages to announce their presence and provide crucial network configuration parameters to neighboring hosts. However, attackers can exploit this by spoofing RA messages to trick hosts into using a rogue router as their default gateway. This can lead to serious security breaches, such as traffic interception, man-in-the-middle (MitM) attacks, and unauthorized network access. RA spoofing attacks can be particularly damaging in environments where hosts trust RA messages implicitly and do not perform proper router validation.
Duplicate Address Detection (DAD) Spoofing: Duplicate Address Detection (DAD) is a mechanism in IPv6 that ensures the uniqueness of IPv6 addresses within a network segment. When a host configures a new IPv6 address, it performs DAD to verify that it is not already used. Attackers can spoof DAD messages to falsely claim ownership of IPv6 addresses, leading to address conflicts and disruption of network communication. DAD spoofing attacks can cause denial of service (DoS) conditions, network instability, and traffic interception.
Neighbor Discovery Protocol (NDP) Cache Poisoning: NDP maintains a cache of neighbor information, including mappings between IPv6 and MAC addresses (IPv6 Neighbor Cache). Attackers can poison the NDP cache by sending fraudulent messages containing forged or malicious information. For example, attackers can associate their MAC address with a legitimate IPv6 address, redirect traffic intended for the legitimate host to their machine, and intercept or manipulate the traffic. NDP cache poisoning attacks can be used maliciously, including traffic interception, session hijacking, and network surveillance.