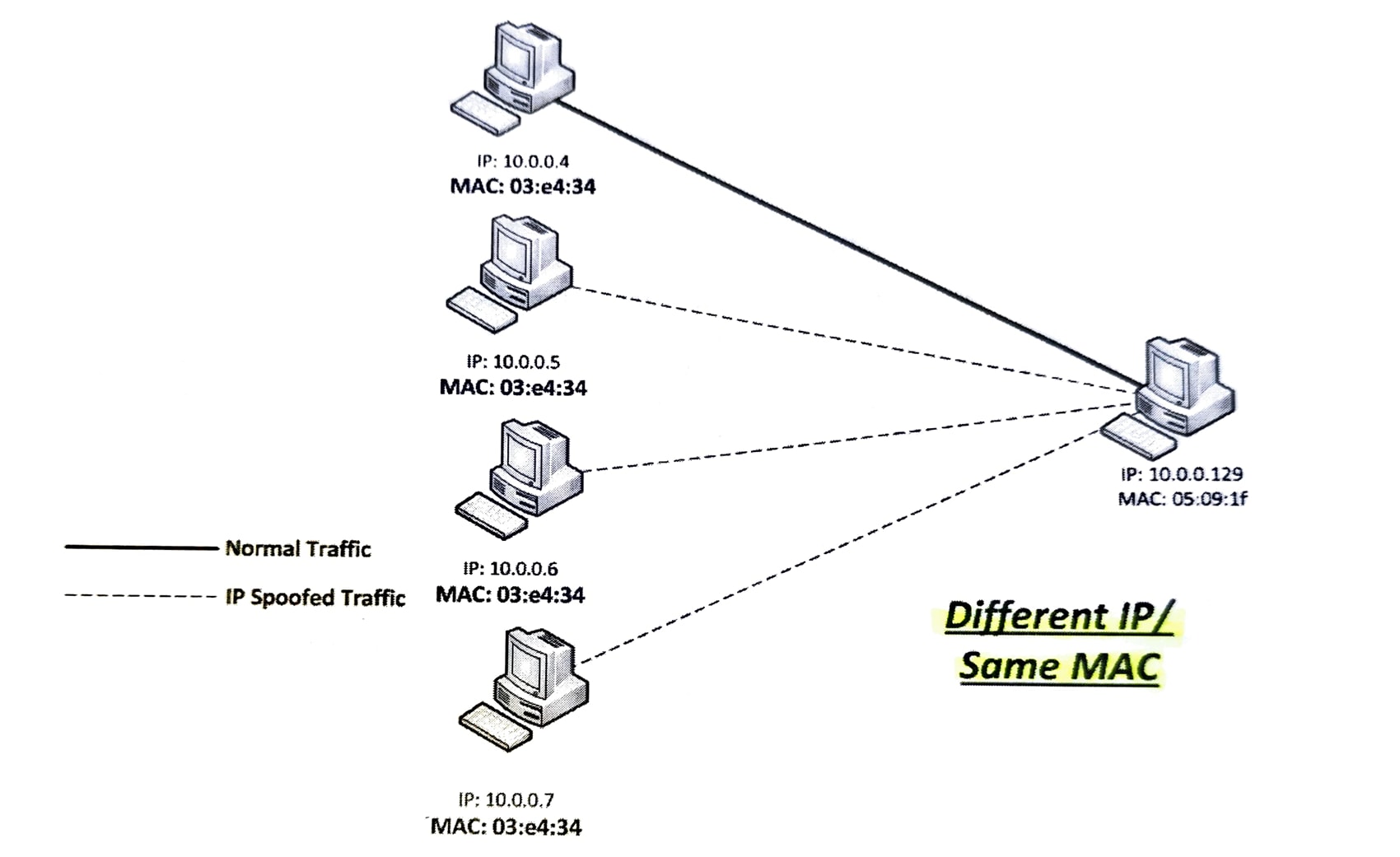
IP Spoofing¶
Attackers use IP spoofing to change their source IP to masquerade as another host(s). In the following image, a Nmap stealth scan was performed from 10.0.0.4 to 10.0.0.129 port 80 with the decoy option enabled. The IPs spoofed from 10.0.0.4 are: 10.0.0.5, 10.0.0.6, and 10.0.0.7.