IPv6 Vulnerabilities¶
IPv6, the next-generation Internet Protocol, introduces various enhancements over IPv4, including a larger address space, improved security features, and better support for mobility and Quality of Service (QoS). However, IPv6 also brings its own set of vulnerabilities and security challenges. Here are some common IPv6 vulnerabilities:
IPV6 Vulnerabilities¶
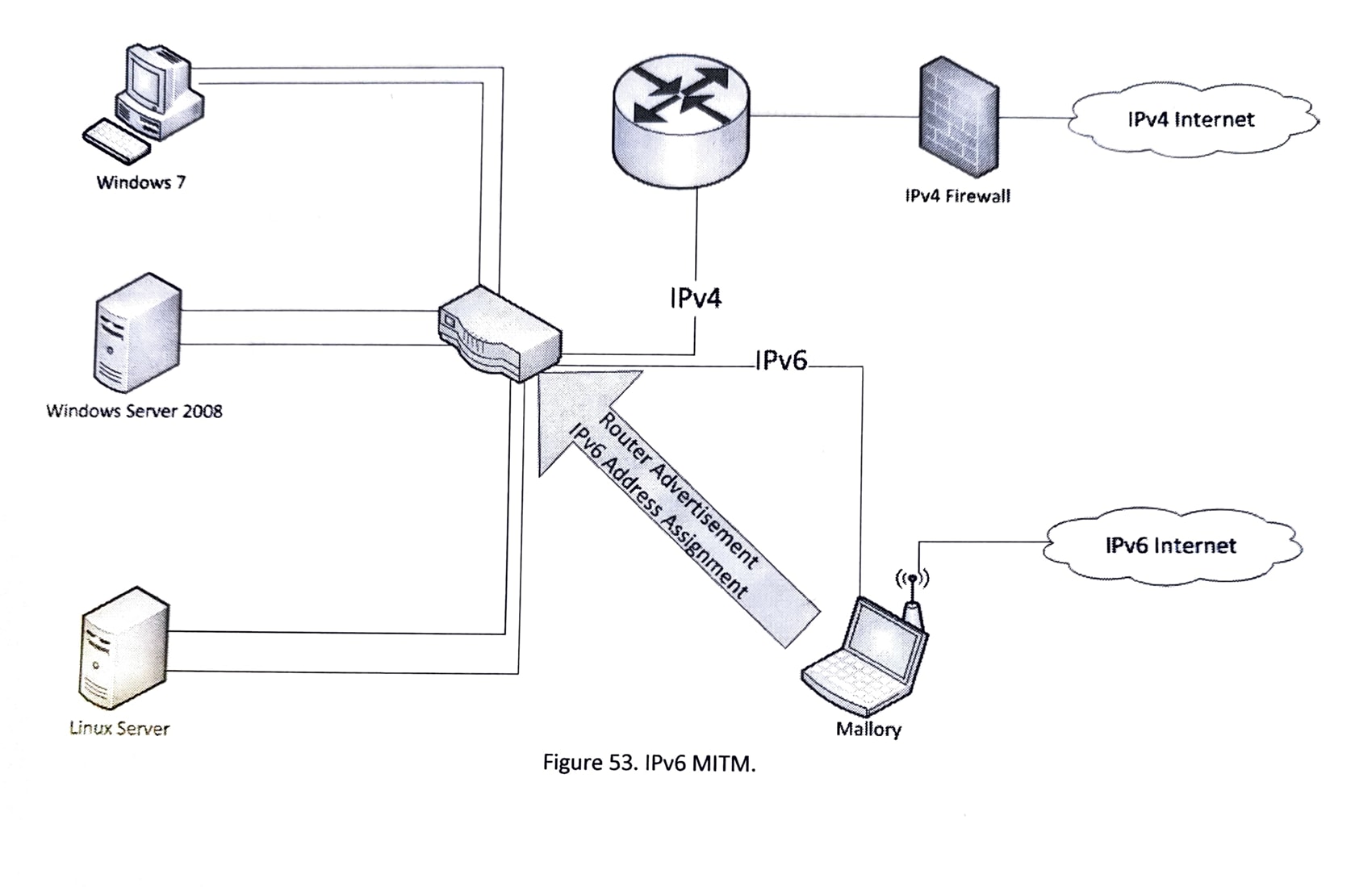
Where IPv4 hosts must rely on manual configuration or DHCP to provide the address of a default gateway, IPV6 hosts can automatically locate default routers on the link. This is accomplished using ICMPv6 messages: Router Solicitation(type 133) and Router Advertisement (type 134). When first joining a link, an IPv6 host multicasts a router solicitation to all routers multicast group. Each router active on the link responds by sending a router advertisement with its address to the group of all nodes.
-
Misconfigured or Unprotected Transition Mechanisms: During the transition from IPv4 to IPv6, many networks deploy transition mechanisms such as 6to4, Teredo, and ISATAP to facilitate communication between IPv4 and IPv6 hosts. Misconfigurations or lack of security controls in these transition mechanisms can lead to vulnerabilities, such as IPv6 tunneling attacks, packet sniffing, and man-in-the-middle (MitM) attacks.
-
Address Spoofing and Neighbor Discovery Protocol (NDP) Attacks: IPv6 Neighbor Discovery Protocol (NDP) is responsible for address autoconfiguration, neighbor discovery, and address resolution functions. Attackers can exploit weaknesses in NDP to perform address spoofing attacks, Router Advertisement (RA) spoofing, Duplicate Address Detection (DAD) spoofing, and Neighbor Discovery Protocol (NDP) cache poisoning attacks.
-
Fragmentation and Reassembly Attacks: IPv6 allows packets to be fragmented and reassembled at the destination. Attackers can exploit fragmentation vulnerabilities to launch fragmentation-based attacks, such as IPv6 fragmentation attacks, where malicious payloads are split across multiple fragments to evade detection and inspection by security devices.
-
Routing Header (RH) and Type 0 Routing Header Vulnerabilities: IPv6 Routing Header (RH) allows packets to specify a list of intermediate nodes that the packet should traverse. Type 0 Routing Header was deprecated due to security concerns, but legacy systems may still accept packets containing it. Attackers can exploit RH vulnerabilities to launch RH-based attacks, such as IPv6 RH0 (Type 0 Routing Header) attacks, where attackers can bypass network security controls and perform source routing.
-
Address Space Exhaustion and DoS Attacks: While IPv6 provides a significantly larger address space than IPv4, it is not immune to address space exhaustion attacks. Attackers can still exhaust network resources by generating a large number of IPv6 addresses or by launching denial-of-service (DoS) attacks against IPv6 infrastructure components, such as routers, switches, and DNS servers.
-
Inadequate IPsec Implementation: IPv6 mandates the support of IPsec for secure communication. However, inadequate or misconfigured IPsec implementations can lead to vulnerabilities such as weak encryption, authentication bypass, or lack of secure key management.
-
Lack of IPv6 Awareness and Security Controls: Many organizations need to gain awareness of IPv6 security risks and implement appropriate security controls for IPv6-enabled networks. This includes inadequate IPv6 firewall rules, intrusion detection and prevention systems (IDS/IPS), security policies, and monitoring mechanisms.
Man-in-the-Middle¶
IPv6-enabled nodes always listen to router advertisements since IPv6 auto-configure is enabled by default. If a rogue router announcement is present, it can open the network to a MITM attack based on the protocol's inability to differentiate between a normal and a rogue router. Additionally, many software programs allow users to advertise as an IPv6 router.