Network Scan Methodologies¶
What is Port Scanning?¶
Port scanning identifies open ports on a target device by sending packets to the device's IP address or hostname/domain name.
Knowing the device you scan by IP or hostname is essential in network reconnaissance.
When it comes to port scanning, TCP is the most commonly used protocol. However, it's important to note that UDP can also be utilized, but only with root privileges. This distinction is key to understanding the different uses of these protocols in the context of port scanning. Port numbers range from 0 to 65535, with 0 - 1023 defined as well-known ports and the rest available for dynamic use by applications.
✏️ Note: Services are not guaranteed at their designated ports; some services can be configured on separate ports
What is a Port?¶
Ports serve as a software abstraction to differentiate communication channels, akin to how IP addresses identify machines on networks. They specifically identify applications running on a single machine. For instance, web browsers typically connect to TCP port 80 for HTTP URLs, and if the secure HTTPS protocol is specified, the browser defaults to port 443.
Since many popular services are associated with specific well-known port numbers, it's often possible to deduce the services represented by open ports. Nmap, for example, incorporates a nmap-services file that catalogs the well-known service associated with registered port and protocol numbers, including ports commonly used by trojan backdoors and other applications that neglect registration with the Internet Assigned Numbers Authority (IANA).
Types of Ports¶
Well-Known¶
Well-known ports, which are reserved by the Internet Assigned Numbers Authority (IANA), are crucial in the world of networking. Ranging from 1 to 1,023, these ports are associated with specific services. For instance, port 22 is commonly used for SSH, port 25 for SMTP, and port 80 for HTTP. Understanding these well-known ports is a key part of network administration and security.
Registered¶
Registered ports include those within the range of 1,024 to 49,151, and much like well-known ports, the IANA designates them; the primary distinction is that unprivileged users can bind to these ports and operate services on their registered port numbers.
Dynamic/Private¶
Dynamic/Private ports, as the name suggests, are more flexible. The Internet Assigned Numbers Authority (IANA) designates port numbers from 49152 through 65535 for dynamic purposes, as explained in the ephemeral ports section. These ports are not tied to specific services and can be used as needed. Additionally, proprietary services exclusive to a particular company may also utilize these ports, making them a versatile option for networking.
Port States¶
-
Open: The service/application on the port is running and actively accepting communications. Finding these is often the primary goal of port scanning. Security-minded people know that each open port is an avenue for attack.
-
Closed: The port is accessible but not accepting connections. No service is running, but the host is reachable.
-
Filtered: A firewall or other security device blocks the probe; the port is unreachable, and typically, no response is received. The scanner cannot determine whether the port is open because packet filtering prevents its probes from reaching it. The filtering could be from a dedicated firewall device, router rules, or host-based firewall software. These ports frustrate attackers because they provide so little information. Sometimes, they respond with ICMP error messages such as type 3 code 13 (destination unreachable: communication administratively prohibited), but filters that drop probes without responding are far more common. Filtering forces the scanner to retry several times to account for dropped probes due to network congestion rather than filtering. Filtering slows down the scan dramatically.
-
Unfiltered: - The unfiltered state means a port is accessible, but the scanner cannot determine whether it is open or closed. Only the ACK scan, which maps firewall rulesets, classifies ports into this state. Scanning unfiltered ports with other scan types, such as a Window, SYN, or FIN scan, may help resolve the port's state.
-
Open|Filtered: - A scanner would place a port in this state when it cannot determine whether it is open or filtered. This occurs for scan types in which open ports give no response. The lack of response could also mean that a packet filter dropped the probe or any response it elicited. Therefore, the scanner does not know whether the port is open or being filtered. The UDP, IP protocol, FIN, NULL, and Xmas scans classify ports this way.
-
Closed|Filtered: Occurs when a scanner cannot determine whether a port is closed or filtered.
✏️ Note: Of these, you will most encounter open, closed, and filtered.
Host Discovery¶
Ping Scanning¶
One of the first steps in any network reconnaissance mission is to reduce a (sometimes huge) set of IP ranges into a list of active or interesting hosts.
In the past, determining if an IP address belonged to an active host was simple: just send an ICMP echo request (ping) packet and wait for a response. However, due to security concerns, many administrators now block ICMP ping messages, despite the RFC requirement that every host must implement an ICMP Echo server function to respond to Echo Requests with corresponding Echo Replies. Nmap offers a wide variety of host discovery techniques beyond the standard ICMP echo request.
TCP SYN Ping (-PS )¶
The -PS option sends an empty TCP packet with the SYN flag set. The default destination port is 80 but an alternate port can be specified as a parameter. A list of ports may be specified in which case probes will be attempted against each port in parallel.
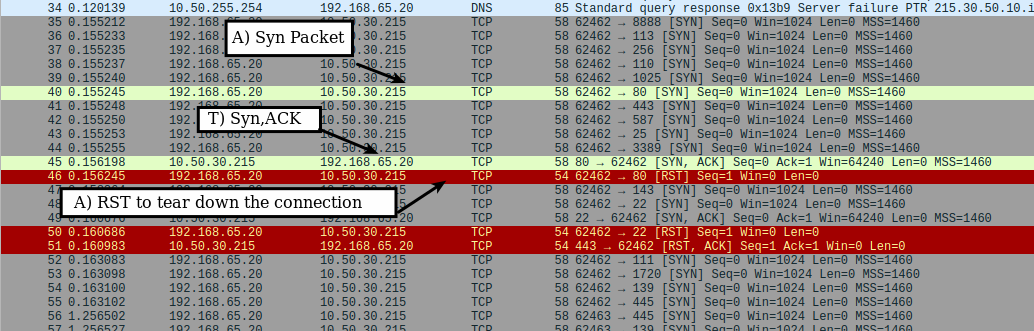
The SYN flag suggests to the remote system that you are attempting to establish a connection. If the destination port will be closed, and a RST (reset) packet will be sent back. If the port happens to be open, the target will take the second step of a TCP three-way-handshake by responding with a SYN/ACK TCP packet. The machine running Nmap then tears down the nascent connection by responding with a RST rather than sending an ACK packet which would complete the three-way-handshake and establish a full connection.
On Unix boxes, only the privileged user root is generally able to send and receive raw TCP packets. For unprivileged users, a workaround is automatically employed whereby the connect system call is initiated against each target port.
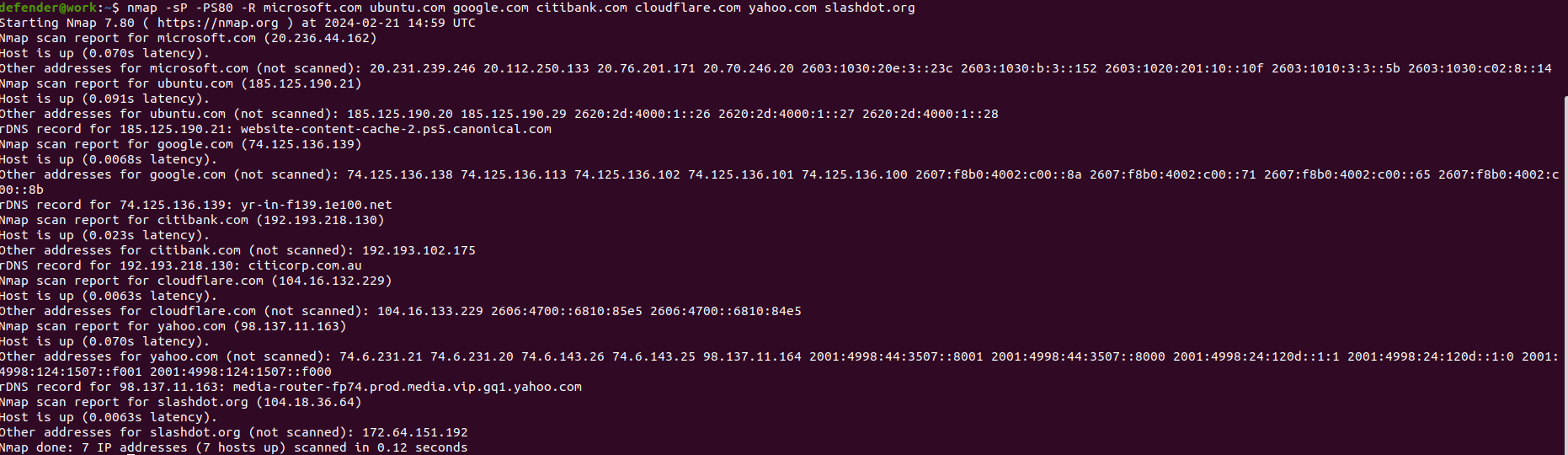
nmap -sP -PS80 -R microsoft.com ubuntu.com google.com citibank.com cloudflare.com yahoo.com slashdot.org
TCP ACK Ping {-PA)¶
The TCP ACK ping operates similarly to the SYN ping, with the key distinction being the use of the TCP ACK flag instead of the SYN flag. While an ACK packet claims to acknowledge data over an established TCP connection, there is actually no such connection. Consequently, remote hosts typically respond with a RST packet, revealing their presence in the process. The -PA option shares the default port (80) with the SYN probe and can also accept a list of destination ports in the same format.
The inclusion of both SYN and ACK ping probes aims to increase the likelihood of circumventing firewalls. Numerous administrators set up routers and basic firewalls to block incoming SYN packets, except those intended for public services such as the company's website or mail server. This configuration restricts incoming connections to the organization but permits users to establish outbound connections to the Internet without hindrance. This stateless method consumes minimal resources on the firewall/router and enjoys broad support from hardware and software filters.When firewall rules such as this are in place, SYN ping probe (-PS) are likely to be blocked when sent toclosed target ports. In such cases, the ACK probe excels by cutting right through these rules.
UDP Ping (-PU)¶
Another method for discovering hosts is the UDP ping, where an empty UDP packet is sent to specified ports. The port list follows the same format as the -PS and -PA options discussed earlier. If no ports are specified, the default is 31,338. The default port is intentionally uncommon because sending packets to open ports is often undesirable for this type of scan.
When a closed port is encountered on the target machine, the UDP probe should trigger an ICMP port unreachable message in response. This indicates to Nmap that the machine is operational and accessible. If an open port is reached, many services simply ignore the empty packet and do not send any response. This is why the default probe port is set to 31,338, a port highly unlikely to be in use.
ICMP Ping Types (-PE, -PP , and -PM)¶
Nmap offers additional host discovery methods beyond TCP and UDP scans. It can utilize ICMP packets similar to those sent by the traditional ping program. Specifically, Nmap sends ICMP type 8 (echo request) packets to target IP addresses and expects type 0 (echo reply) responses from active hosts. However, many hosts and firewalls now block these packets, making ICMP-only scans less reliable for unknown targets over the Internet. Nevertheless, for internal network monitoring by system administrators, this approach can be practical and efficient, enabled with the -PE option.
Furthermore, Nmap extends beyond the standard echo request ICMP ping query. The ICMP standard (RFC 792) defines additional query types such as timestamp request (code 13), information request (code 15), and address mask request (code 17). Although originally intended for obtaining information like address masks and current times, these queries can also serve as host discovery tools. Timestamp and address mask queries can be sent using the -PP and -PM options, respectively.
IP Protocol Ping (-PO)¶
The IP protocol ping is where nmap is sending IP packets with a specified protocol number set in their IP header. If no protocols are specified, the default includes ICMP (protocol 1), IGMP (protocol 2), and IP-in-IP (protocol 4). This method seeks responses using the same protocol as the probe, or ICMP protocol unreachable messages indicating the absence of support for the given protocol by the destination host. Either type of response confirms the target host's existence.
Types of Scans¶
SYN (Stealth) Scan (Default Scan w/ root privileges)¶
Nmap Stealth Scans are the default scans implemented using root privileges. The scanner sends a TCP SYN packet to the target ports. If a SYN + ACK is received, the scanner immediately sends a RST + ACK packet to terminate the connection forcefully. Stealth scans do not complete the connections and keep log entries to a minimum.
✏️ Note: SYN (Stealth) Scans can also be referred to as Half-Open Scans
- nmap -sS 10.50.0.0/16
- Open Port
- SYN + ACK received from the target; scanner sends a RST to tear down the connection
- Closed Port
- RST + ACK received from target
Connect Scan (Default Scan for Unprivileged User)¶
Nmap Connect Scans fully implements a three-way TCP handshake. Unlike the Stealth Scan, the Connect scan completes the entire connection. Nmap will use this scan type by default when a user does not have raw packet privileges or is scanning IPv6 networks.
-
nmap -sT 10.50.0.0/16
-
Open Port
- SYN + ACK received from the target; scanner sends an ACK followed by a RST + ACK to tear down the connection
-
Closed Port
- RST + ACK received from target
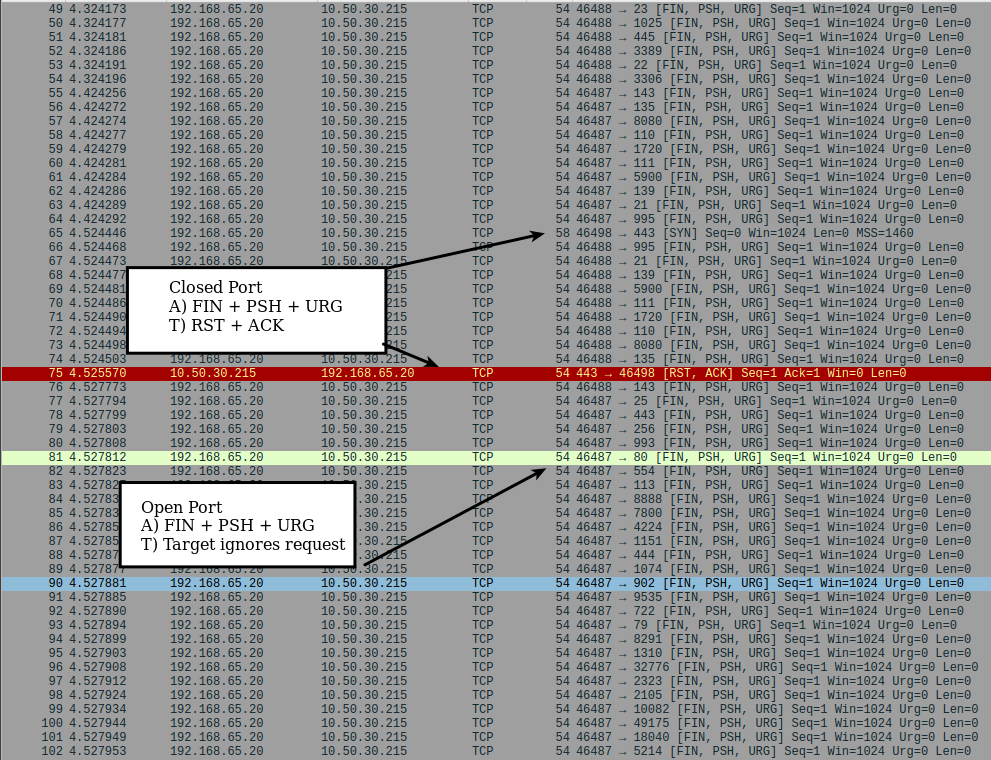
FIN Scan¶
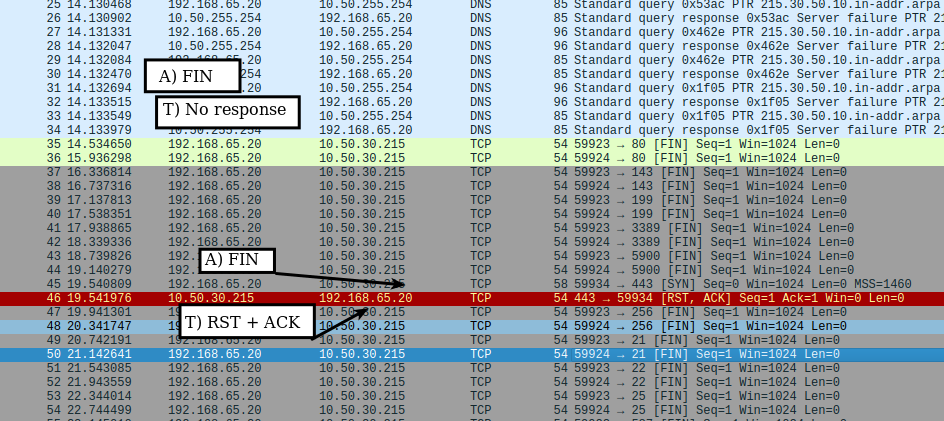
Nmap FIN scans sends a FIN to target ports. If the target ignores the request, the port is open. If the port is closed, the target sends a RST.
- nmap -sF 10.50.0.0/16
- Open Port
- Target ignores request
- Closed Port
- RST+ACK received from target
✏️ Note: The server in the following pcap has an http server on port 80. A listening port on 443 is active without a service or application running and processing data received, and it is also defined as a closed port.
🤿 Deep Dive! Some modern operating systems have implemented specific measures to prevent or minimize the effectiveness of this scanning technique. For example, Windows Vista, Windows 7, Windows Server 2008, and later versions of these operating systems have implemented a feature called TCP/IP stack hardening that makes them less vulnerable to FIN scan enumeration. This feature changes how the operating system handles unsolicited FIN packets, making it more difficult for attackers to use this scanning technique to determine the status of a port. Windows 200 platforms and above will always send a RST Similarly, some Linux distributions, such as Red Hat Enterprise Linux and CentOS, have implemented a feature called TCP/IP stack hardening that provides similar protection against FIN scan enumeration. This feature includes a mechanism called tcp_fin_timeout that determines how long a FIN packet can stay in the system’s memory before being discarded.
Null Scan¶
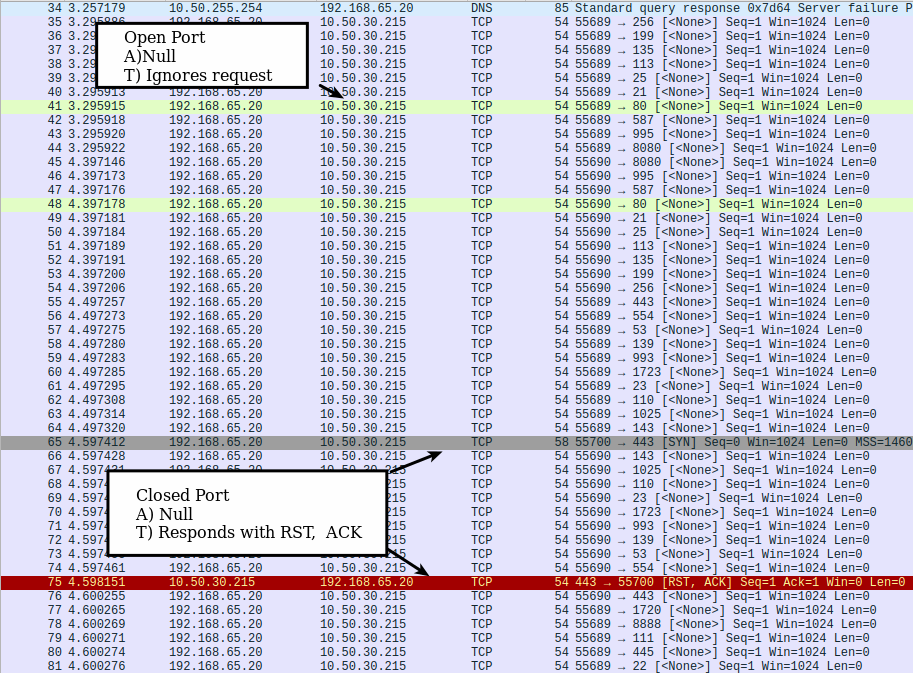
Nmap Null scans sets no TCP control flags and sends a null packet to target ports. - nmap -sN 10.50.0.0/16 - Open Port - Target ignores request - Closed Port - RST + ACK received from target
✏️ Note: Windows 2000 and above will always send a RST Packet
✏️ Note: The server in the following pcap has an http server on port 80. A listening port on 443 is active without a service or application running and processing data received, and it is also defined as a closed port.
Xmas Scan¶
An XMAS scan sends packets with the FIN, PSH, and URG flags set, making the packet resemble a 'lit-up' Christmas tree, hence the name. This scan technique exploits the behavior of TCP/IP stack implementations in various operating systems. A closed port will respond with an RST (reset) packet. In contrast, an open port will ignore the packet, making it a valuable method for detecting open ports without establishing a connection. However, it's only sometimes effective against modern firewalls and IDS/IPS systems that can detect and block such scans. - nmap -sX 10.50.0.0/16 - Open Port - Target ignores request - Closed Port - RST + ACK Received
✏️ Note: The server in the following pcap has an http server on port 80. A listening port on 443 is active without a service or application running and processing data received, and it is also defined as a closed port.
ARP Scan¶
One common scenario for using Nmap is to conduct a scan of an Ethernet LAN. In such LANs, especially those utilizing private address ranges according to RFC 1918, a large portion of IP addresses typically remain unused. When Nmap attempts to transmit a raw IP packet like an ICMP echo request, the operating system needs to determine the destination hardware (ARP) address associated with the target IP address to properly address the Ethernet frame. This process necessitates issuing a series of ARP requests.