Man in the Middle (IPv4)¶
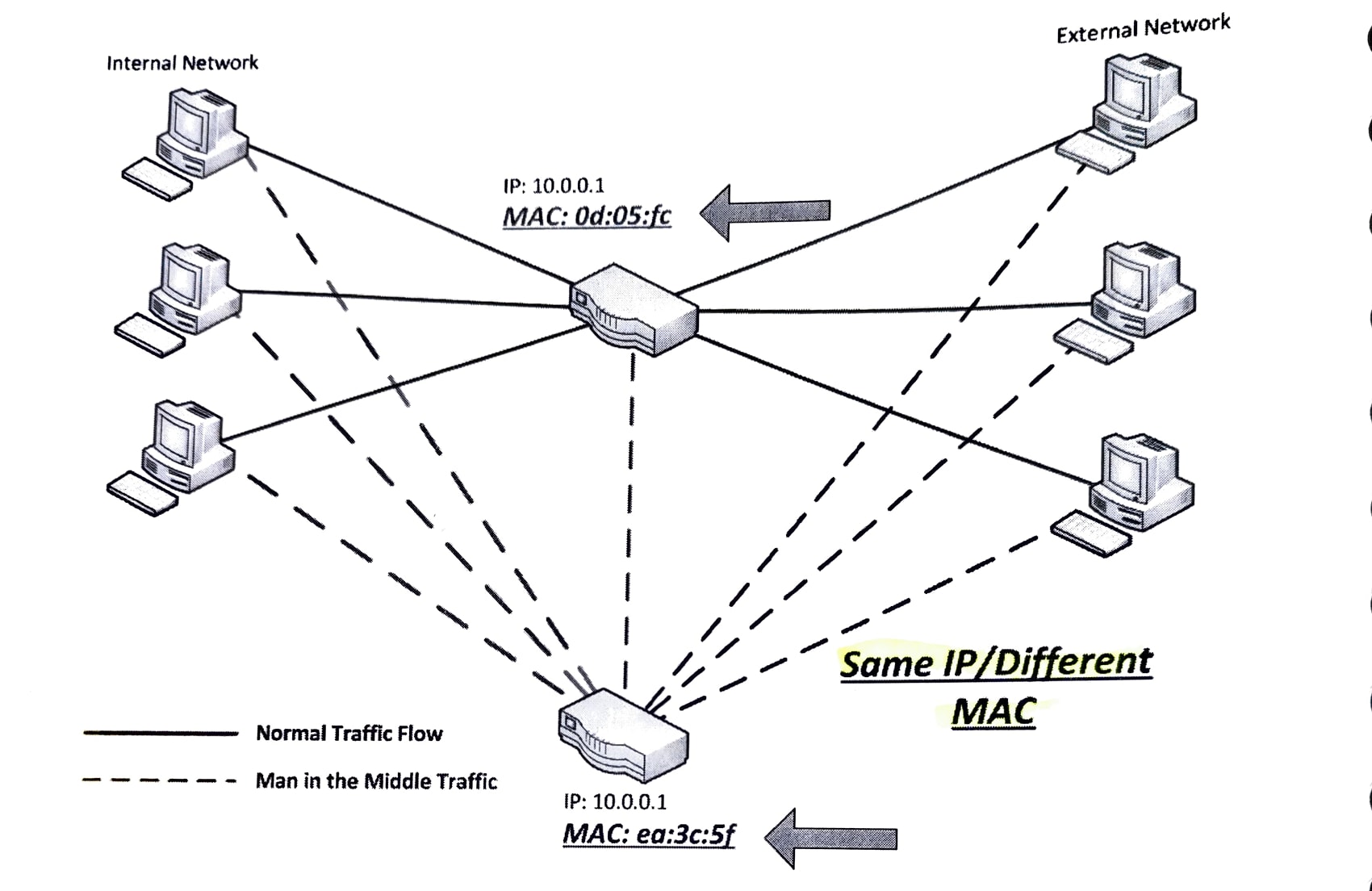
The Man in the Middle technique allows attackers to read and possibly modify messages between two parties without the user’s knowledge. The network diagram below depicts the correct IPs and their associated MAC addresses.
-
The malicious computer will send a reply processed by the router and victim machine, updating their Address lookup table.
-
Whenever information is passed, the malicious machine will be the first to receive and process the packets.
- Certain programs can quickly process information and manipulate data in real-time.