TLS/SSL¶
TLS (Transport Layer Security) and SSL (Secure Sockets Layer)¶
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are cryptographic protocols designed to provide secure communication over a computer network, most commonly the internet. These protocols establish an encrypted connection between a client and a server to ensure that data exchanged between them remains confidential and cannot be tampered with by unauthorized parties. Keep in mind, TLS evolved from SSL so those terms are often used interchangeably. (TLS is the industry standard!)
Breakdown of how TLS/SSL works:¶
-
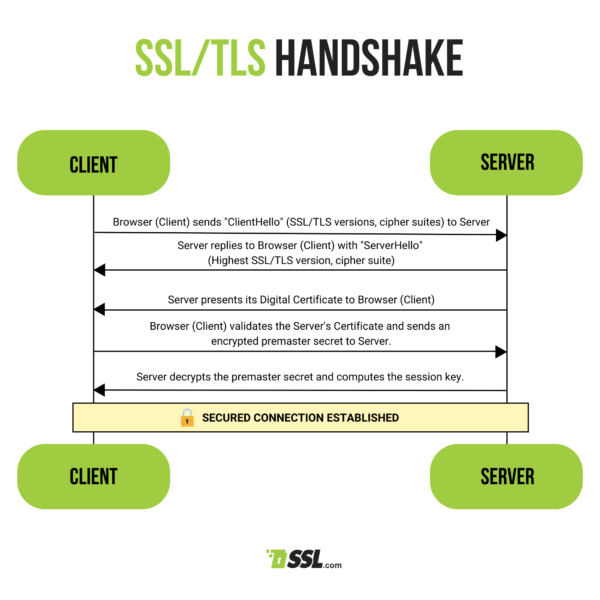
Handshake: The client initiates a connection to the server and requests a secure connection. The server responds by sending its digital certificate to the client.
-
Certificate verification: The client verifies the authenticity of the server's certificate. This involves checking if the certificate was issued by a trusted Certificate Authority (CA) and if it has not expired. If the certificate is valid and trusted, the client proceeds to the next step. (We will discuss Certificate Authorities further in depth in lesson 06)
-
Key exchange: The client and server negotiate and agree upon cryptographic parameters, including the algorithms and keys to be used for encryption and authentication during the session. This process ensures that only the client and server can understand the encrypted data.
-
Encryption: Once the parameters are agreed upon, the actual data transmission begins. All data exchanged between the client and server is encrypted using symmetric encryption, where both parties use the same key to encrypt and decrypt data. This ensures confidentiality.
-
Data integrity: In addition to encryption, TLS/SSL also ensures data integrity. This means that even if an attacker intercepts the encrypted data, they cannot modify it without being detected. This is achieved through cryptographic hashing algorithms and digital signatures.
TLS/SSL operates at the transport layer of the OSI model, sitting between the application layer and the network layer. It is widely used to secure various types of internet communication, including web browsing, email, instant messaging, and file transfer.