Symmetric Key Algorithms¶
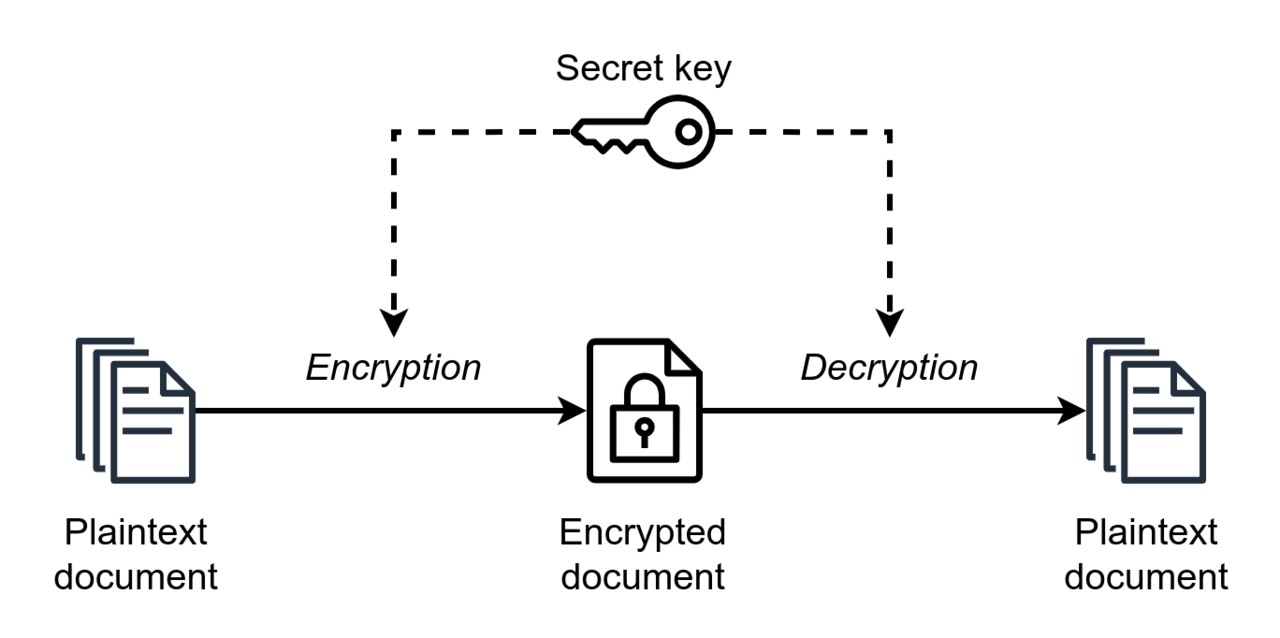
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext.
The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption. However, symmetric-key encryption algorithms are usually better for bulk encryption.
Diffusion and confusion¶
-
Diffusion and confusion are two fundamental principles in modern symmetric key cryptography.
-
Diffusion aims to spread the influence of plaintext bits over the entire ciphertext, while confusion aims to make the relationship between the plaintext and the ciphertext as complex as possible.
- Techniques such as substitution (substituting elements of the plaintext), permutation (reordering elements), and expansion (expanding the data) contribute to achieving diffusion and confusion in encryption algorithms like Advanced Encryption Standard (AES).
- Diffusion = (Transposition or Permutation)
abcd → dacb
- Example : DES
- Confusion = (Substitution)
a → b
- Example : Caesar Cipher
- Diffusion = (Transposition or Permutation)
abcd → dacb
Types¶
Stream ciphers encrypt the digits (typically bytes), or letters (in substitution ciphers) of a message one at a time. Examples include ChaCha20.
Block ciphers take a number of bits and encrypt them in a single unit, padding the plaintext to achieve a multiple of the block size. Examples include AES & two fish .
For further understanding of Stream and Block ciphers, view the link below:
Triple Data Encryption Stadard (3DES)¶
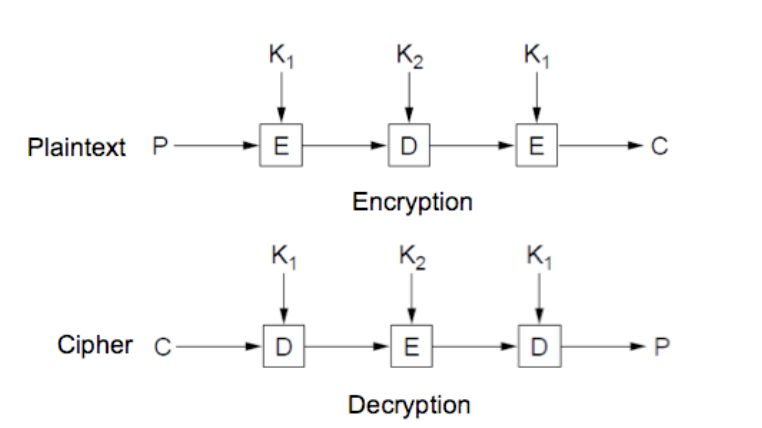
3DES is the successor to the Data Encryption Standard (DES). 3DES has two modes of operation: 3DES-EEE and 3DES-EDE.
- 3DES-EEE uses three keys for an effective key strength of 168 bits
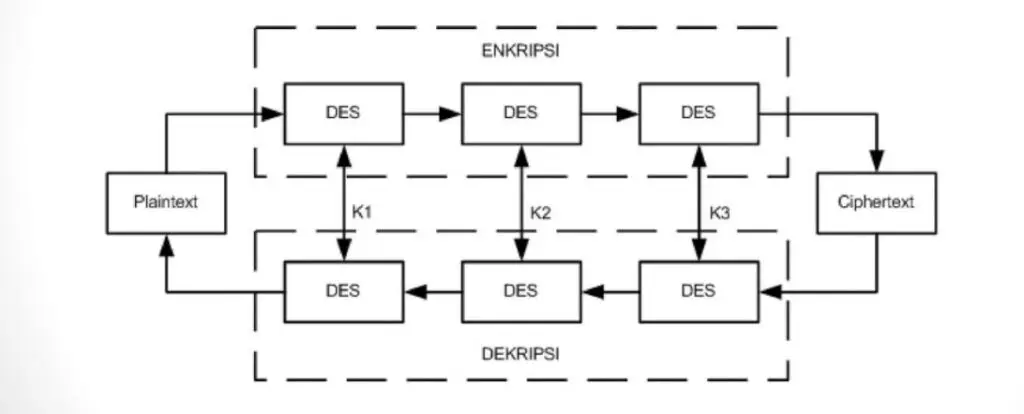 - 3DES-EDE uses two of the same keys for encryption and a part decryption key for scrambling the ouput.
- 3DES-EDE uses two of the same keys for encryption and a part decryption key for scrambling the ouput.
Points to remember¶
- 3DES is a block cipher.
- The key size is 112 or 168 bits
- Encrypts data in blocks of 64 bits
- Due to vulnerabilities with 3DES's encryptioin algorithm and inadequate key size, NIST deprecated 3DES in 2019 and was replaced with the more secure and robust AES.
Advanced Encryption Standard (AES)¶
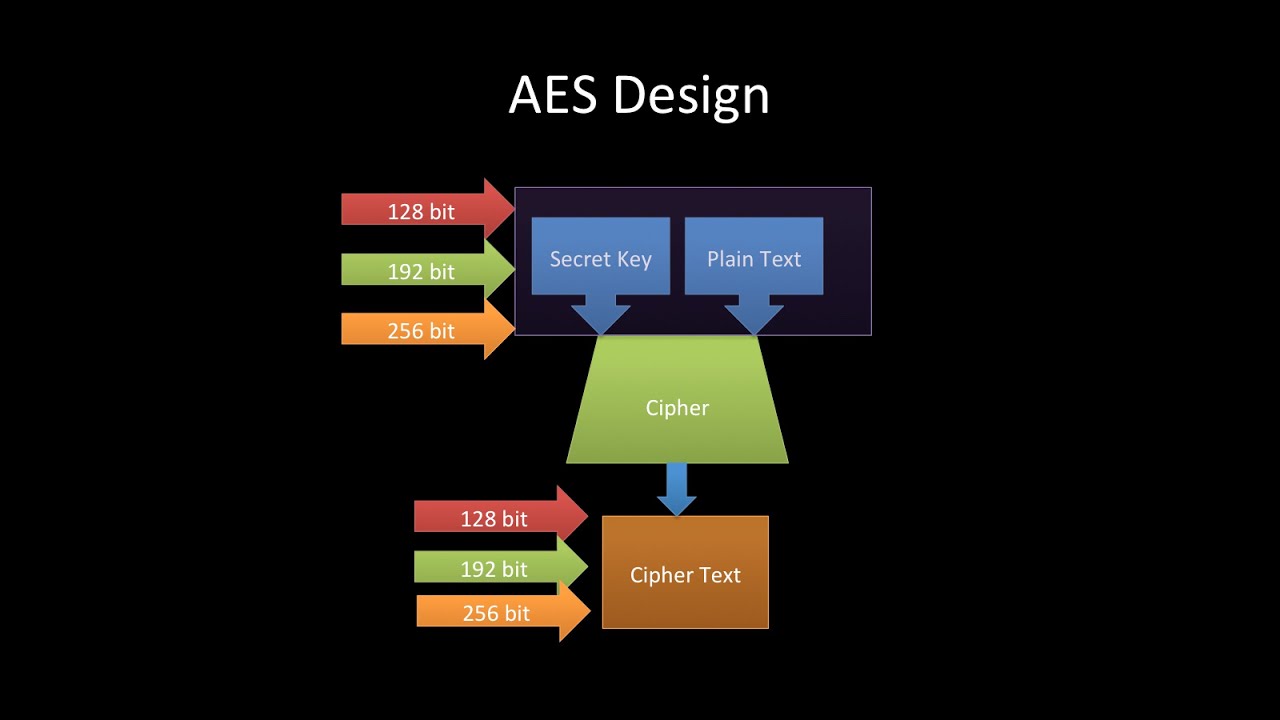
AES is a specification for the encryption of electronic data established by the U.S National Institute of Standards and Technology (NIST) in 2001. This is the most widely used symmetric encryption algorithm in the world. It is used by the U.S. government, banks, and other organizations to protect sensitive data. AES is considered to be very secure, and it is resistant to a wide range of attacks.
Points to remember¶
- AES is a block cipher.
- The key size can be 128/192/256 bits.
- Encrypts data in blocks of 128 bits each.
That means it takes 128 bits as input and outputs 128 bits of encrypted cipher text. AES relies on substitution-permutation network principle which means it is performed using a series of linked operations which involves replacing and shuffling of the input data.
Applications¶
-
Wireless security: AES is used in securing wireless networks, such as Wi-Fi networks, to ensure data confidentiality and prevent unauthorized access.
-
Database Encryption: AES can be applied to encrypt sensitive data stored in databases. This helps protect personal information, financial records, and other confidential data from unauthorized access in case of a data breach.
-
Secure communications: AES is widely used in protocols such as internet communications, email, instant messaging, and voice/video calls. It ensures that the data remains confidential.
-
Data storage: AES is used to encrypt sensitive data stored on hard drives, USB drives, and other storage media, protecting it from unauthorized access in case of loss or theft.
-
Virtual Private Networks (VPNs): AES is commonly used in VPN protocols to secure the communication between a user’s device and a remote server. It ensures that data sent and received through the VPN remains private and cannot be deciphered by eavesdroppers.
-
Secure Storage of Passwords: AES encryption is commonly employed to store passwords securely. Instead of storing plaintext passwords, the encrypted version is stored. This adds an extra layer of security and protects user credentials in case of unauthorized access to the storage.
-
File and Disk Encryption: AES is used to encrypt files and folders on computers, external storage devices, and cloud storage. It protects sensitive data stored on devices or during data transfer to prevent unauthorized access.
Twofish¶
Twofish is a symmetric key block cipher, a contender for the Advanced Encryption Standard (AES) but ultimately not chosen. Here's a breakdown:
- Block Cipher: It operates on fixed-size data blocks (128 bits in Twofish) during encryption and decryption.
- Symmetric Key: The same key is used for both encryption and decryption.
- Variable Key Size: Twofish offers flexibility with key sizes of 128, 192, or 256 bits, depending on the desired security level.