Asymmetric Key Algorithms or Public key Cryptogophy¶
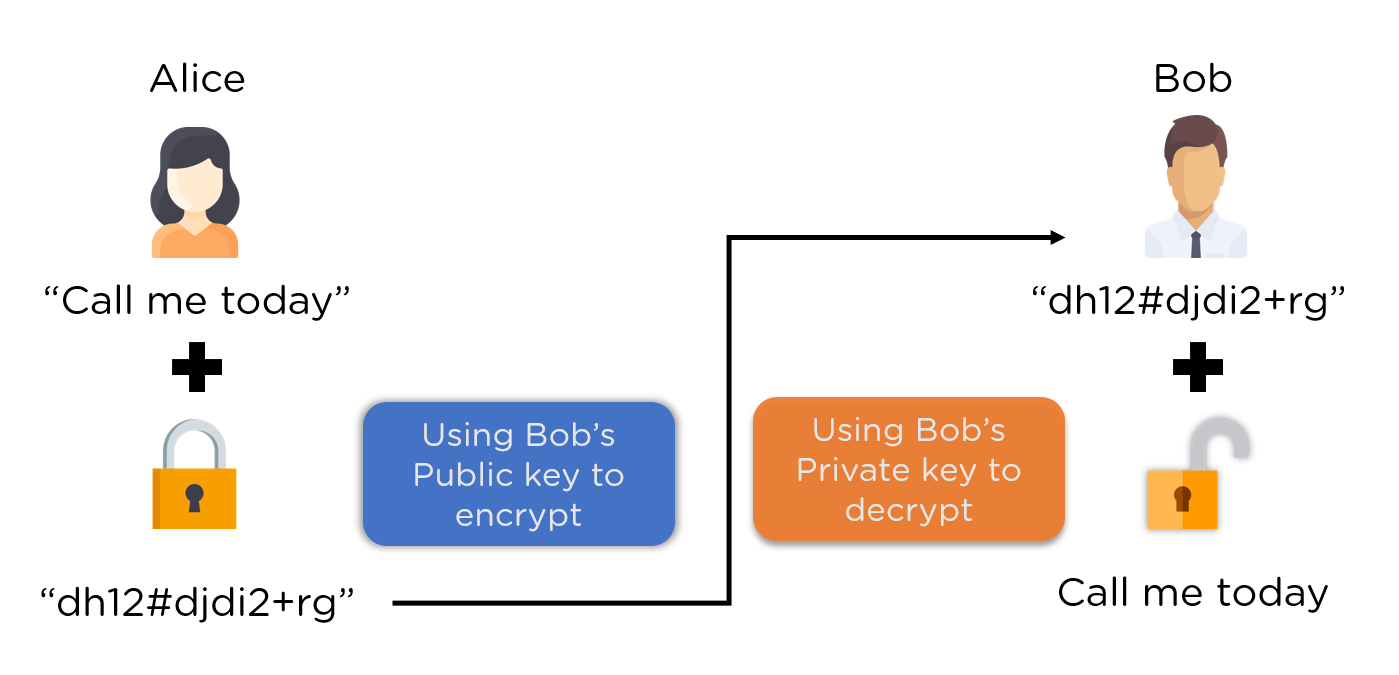
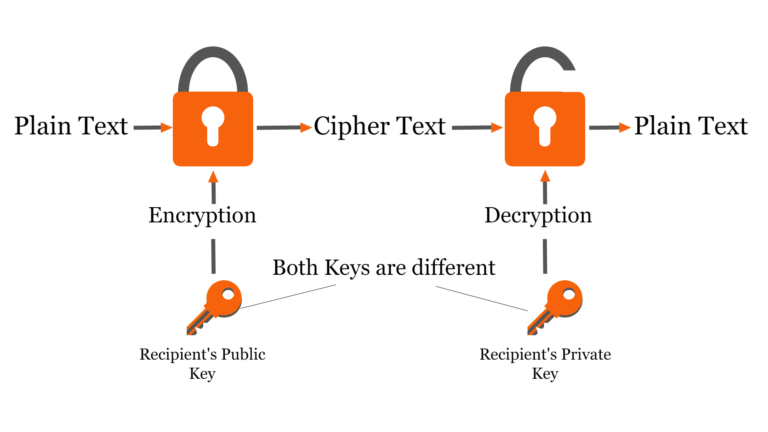
In an asymmetric cryptographic process one key is used to encipher the data, and a different but corresponding key is used to decipher the data. A system that uses this type of process is known as a public key system. The key that is used to encipher the data is widely known, but the corresponding key for deciphering the data is a secret.
- Public Lock: Anyone can open it to put something in (encrypt messages for you).
- Private Lock: Only you have the key to open what's inside (decrypt messages sent to you).
How it Works:¶
-
Someone wants to send you a secret message: They use your publicly available public key to encrypt the message. This scrambles the message so only someone with the matching private key can understand it.
-
The encrypted message arrives: Only your private key can decrypt the message, turning it back into its original form.
Advantages of Asymmetric Keys:¶
-
Secure Communication: Anyone can send you encrypted messages without needing a shared secret key beforehand.
-
Digital Signatures: You can use your private key to "sign" digital documents, proving you created or approved them. Anyone with your public key can verify the signature, ensuring authenticity.
RSA¶
RSA (Rivest–Shamir–Adleman): This is a public-key encryption algorithm that is used to encrypt data that is being sent over the internet. RSA is also used to create digital signatures.
The RSA algorithm involves four steps: key generation, key distribution, encryption, and decryption.
The DSS Public Key Algorithm¶
The U.S. National Institute of Science and Technology (NIST) Digital Signature Standard (DSS) public key algorithm is based on the difficulty of the discrete logarithm problem
A DSS key pair includes a private and a public key. The DSS private key is used to generate a digital signature, and the DSS public key is used to verify a digital signature.
Elliptic Curve Digital Signature Algorithm (ECDSA)¶
The ECDSA algorithm uses elliptic curve cryptography (an encryption system based on the properties of elliptic curves) to provide a variant of the Digital Signature Algorithm.
For further understanding between Symmetric and Asymmetric Encryption, view the link below: